1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
47
48
49
50
51
52
53
54
55
56
57
58
59
60
61
62
63
64
65
66
67
68
69
70
71
72
73
74
75
76
77
78
79
80
81
82
83
84
85
86
87
88
89
90
91
92
93
94
95
96
97
98
99
100
101
102
103
104
105
| from pwn import u64
S_BOX = [
0x29, 0x40, 0x57, 0x6e, 0x85, 0x9c, 0xb3, 0xca, 0xe1, 0xf8, 0xf, 0x26, 0x3d, 0x54, 0x6b, 0x82,
0x99, 0xb0, 0xc7, 0xde, 0xf5, 0xc, 0x23, 0x3a, 0x51, 0x68, 0x7f, 0x96, 0xad, 0xc4, 0xdb, 0xf2,
0x9, 0x20, 0x37, 0x4e, 0x65, 0x7c, 0x93, 0xaa, 0xc1, 0xd8, 0xef, 0x6, 0x1d, 0x34, 0x4b, 0x62,
0x79, 0x90, 0xa7, 0xbe, 0xd5, 0xec, 0x3, 0x1a, 0x31, 0x48, 0x5f, 0x76, 0x8d, 0xa4, 0xbb, 0xd2,
0xe9, 0x0, 0x17, 0x2e, 0x45, 0x5c, 0x73, 0x8a, 0xa1, 0xb8, 0xcf, 0xe6, 0xfd, 0x14, 0x2b, 0x42,
0x59, 0x70, 0x87, 0x9e, 0xb5, 0xcc, 0xe3, 0xfa, 0x11, 0x28, 0x3f, 0x56, 0x6d, 0x84, 0x9b, 0xb2,
0xc9, 0xe0, 0xf7, 0xe, 0x25, 0x3c, 0x53, 0x6a, 0x81, 0x98, 0xaf, 0xc6, 0xdd, 0xf4, 0xb, 0x22,
0x39, 0x50, 0x67, 0x7e, 0x95, 0xac, 0xc3, 0xda, 0xf1, 0x8, 0x1f, 0x36, 0x4d, 0x64, 0x7b, 0x92,
0xa9, 0xc0, 0xd7, 0xee, 0x5, 0x1c, 0x33, 0x4a, 0x61, 0x78, 0x8f, 0xa6, 0xbd, 0xd4, 0xeb, 0x2,
0x19, 0x30, 0x47, 0x5e, 0x75, 0x8c, 0xa3, 0xba, 0xd1, 0xe8, 0xff, 0x16, 0x2d, 0x44, 0x5b, 0x72,
0x89, 0xa0, 0xb7, 0xce, 0xe5, 0xfc, 0x13, 0x2a, 0x41, 0x58, 0x6f, 0x86, 0x9d, 0xb4, 0xcb, 0xe2,
0xf9, 0x10, 0x27, 0x3e, 0x55, 0x6c, 0x83, 0x9a, 0xb1, 0xc8, 0xdf, 0xf6, 0xd, 0x24, 0x3b, 0x52,
0x69, 0x80, 0x97, 0xae, 0xc5, 0xdc, 0xf3, 0xa, 0x21, 0x38, 0x4f, 0x66, 0x7d, 0x94, 0xab, 0xc2,
0xd9, 0xf0, 0x7, 0x1e, 0x35, 0x4c, 0x63, 0x7a, 0x91, 0xa8, 0xbf, 0xd6, 0xed, 0x4, 0x1b, 0x32,
0x49, 0x60, 0x77, 0x8e, 0xa5, 0xbc, 0xd3, 0xea, 0x1, 0x18, 0x2f, 0x46, 0x5d, 0x74, 0x8b, 0xa2,
0xb9, 0xd0, 0xe7, 0xfe, 0x15, 0x2c, 0x43, 0x5a, 0x71, 0x88, 0x9f, 0xb6, 0xcd, 0xe4, 0xfb, 0x12,
]
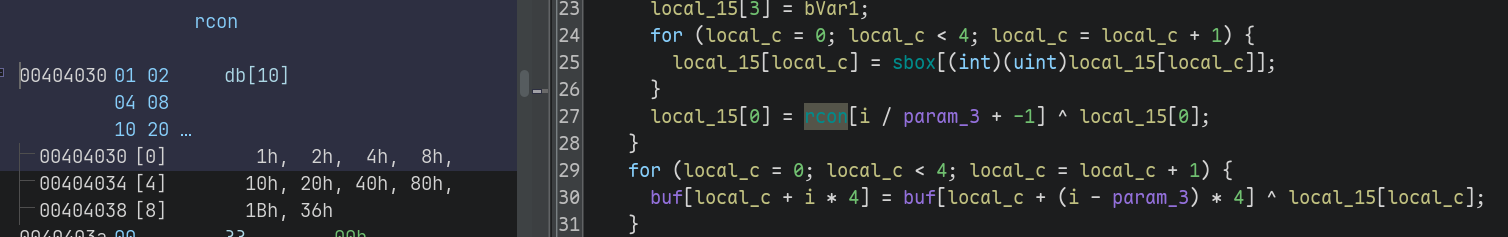
R_CON = [
0x00, 0x01, 0x02, 0x04, 0x08, 0x10, 0x20, 0x40, 0x80, 0x1B, 0x36
]
def sub_bytes(state):
return [S_BOX[b] for b in state]
def shift_rows(s):
return [
s[0], s[5], s[10], s[15],
s[4], s[9], s[14], s[3],
s[8], s[13], s[2], s[7],
s[12], s[1], s[6], s[11]
]
def xtime(a):
return ((a << 1) ^ 0x1B) & 0xFF if a & 0x80 else (a << 1)
def mix_single_column(a):
t = a[0] ^ a[1] ^ a[2] ^ a[3]
u = a[0]
a[0] ^= t ^ xtime(a[0] ^ a[1])
a[1] ^= t ^ xtime(a[1] ^ a[2])
a[2] ^= t ^ xtime(a[2] ^ a[3])
a[3] ^= t ^ xtime(a[3] ^ u)
return a
def mix_columns(s):
for i in range(4):
col = s[i * 4:(i + 1) * 4]
s[i * 4:(i + 1) * 4] = mix_single_column(col)
return s
def add_round_key(s, k):
return [a ^ b for a, b in zip(s, k)]
def key_expansion(key):
key_symbols = list(key)
assert len(key_symbols) == 16
expanded = key_symbols[:]
for i in range(4, 44):
t = expanded[(i - 1) * 4:i * 4]
if i % 4 == 0:
t = t[1:] + t[:1]
t = [S_BOX[b] for b in t]
t[0] ^= R_CON[i // 4]
for j in range(4):
expanded.append(expanded[(i - 4) * 4 + j] ^ t[j])
return expanded
def aes_encrypt_block(block, key):
state = list(block)
w = key_expansion(key)
state = add_round_key(state, w[:16])
for round in range(1, 10):
state = sub_bytes(state)
state = shift_rows(state)
state = mix_columns(state)
state = add_round_key(state, w[round * 16:(round + 1) * 16])
state = sub_bytes(state)
state = shift_rows(state)
state = add_round_key(state, w[160:176])
return bytes(state)
if __name__ == "__main__":
key = b"0123456789ABCDEF"
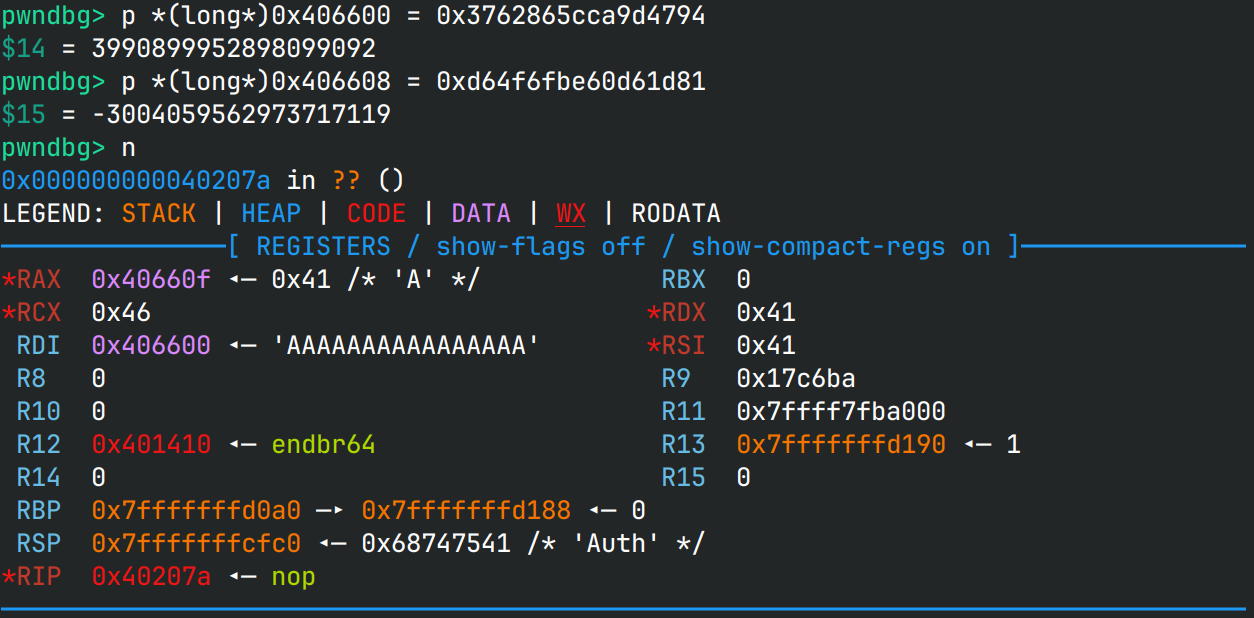
plaintext = b"A" * 16
ciphertext = aes_encrypt_block(plaintext, key)
print("Plain :", plaintext)
print("Cipher:", hex(u64(ciphertext[:8])), hex(u64(ciphertext[8:])))
|