ciscn2024 - Magic VM
文件属性
| 属性 | 值 |
|---|---|
| Arch | x64 |
| RELRO | Full |
| Canary | off |
| NX | on |
| PIE | on |
| strip | no |
| libc | 2.35-0ubuntu3.7 |
解题思路
没去符号表的vm题,费了好大劲在黑灯开始时想通了怎么利用,然后来不及了
我在这里会放逆好的伪代码,看起来清晰多了
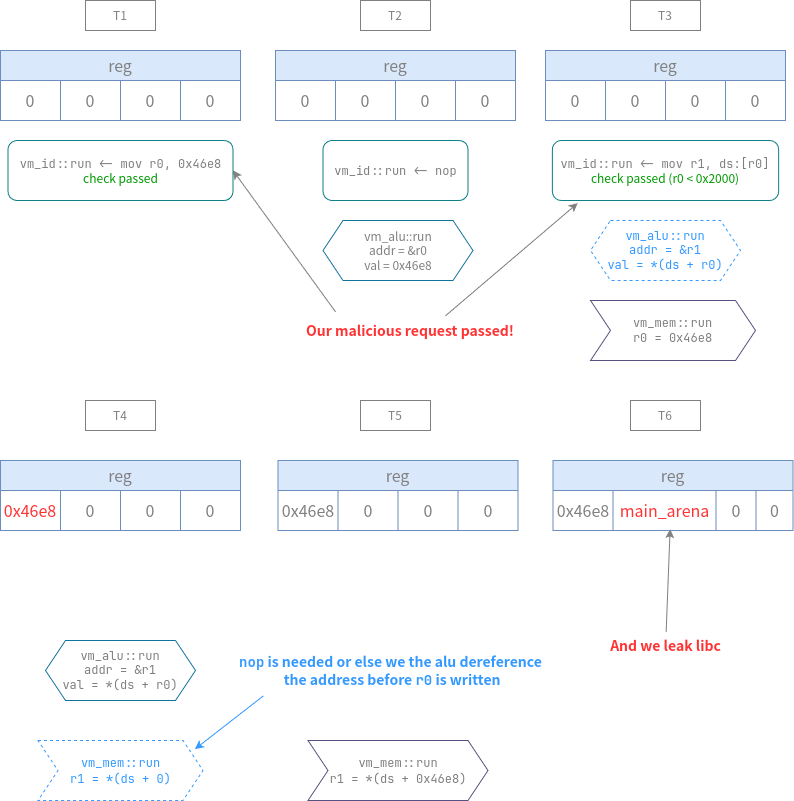
这道题的漏洞在于绕过时序,从代码读入到实际写入,实际上需要3个周期,
而所有合法性检查是在vm_id::run中做的,那意味着,我们只要使数据变化慢于检测,
即可绕过,具体原理如图所示

理解完了这个原理之后,思路就很清楚了:先获取libc和mmap的地址,然后在data段伪造FILE,
设置好apple的触发条件,最后把伪造的FILE挂到_IO_list_all下,等程序自然退出就可以拿shell
为了自动化生成这长长的脚本,我写了对应的汇编和汇编器附在文后
Extra Bonus
- 我们拿到的mmap段紧邻另一段,而在里面有libc,有自身所在的地址,这不是巧合,它是TLS段
cout <<也有"hook"可用,在这个libstdc++中,在执行输出时,会解析函数,即导入函数到got表中, 那么由于它没有开Full RELRO,所以我们还可以写got表来跳转任意代码,但前提是我们能拿到libstdc++的地址- 由于延迟赋值的特性(见上图),所以在
mov reg, imm和mov ds:[reg], reg这样的语句中间必须有一个等待周期, 可以nop,或者先处理其他寄存器
EXPLOIT
1 | ; exp.asm |
1 | # assembler.py |
1 | # vm.py |
- 标题: ciscn2024 - Magic VM
- 作者: RocketDev
- 创建于 : 2024-05-21 00:48:00
- 更新于 : 2024-07-25 12:34:56
- 链接: https://rocketma.dev/2024/05/20/vm/
- 版权声明: 本文章采用 CC BY-NC-SA 4.0 进行许可。
评论