hgame2024 week2 剩余题解
12 challenges solved
web
What the cowsay?
the cow want to tell you something
cowsay命令,填入字符串,尝试后发现为命令绕过
经尝试,cat、flag、|等会被拦下来,那么换行可不可以呢?
当然,做出来了就是可以了;在用""包围字符串绕过字符检测,尝试使用
%0a"ca"t "fl"ag来获取flag,错误!
ls一下根目录,发现有一个flag_is_here,尝试cat一下,还是失败,ls -hls,发现是路径
终于在里面找到了flag
1 | $ curl http://106.14.57.14:31942/post -d 'user_input=%0a"ca""t" /"fl"ag_is_here/"fl"ag_c0w54y' |
reverse
babyre
一道多线程题,坑还挺多的
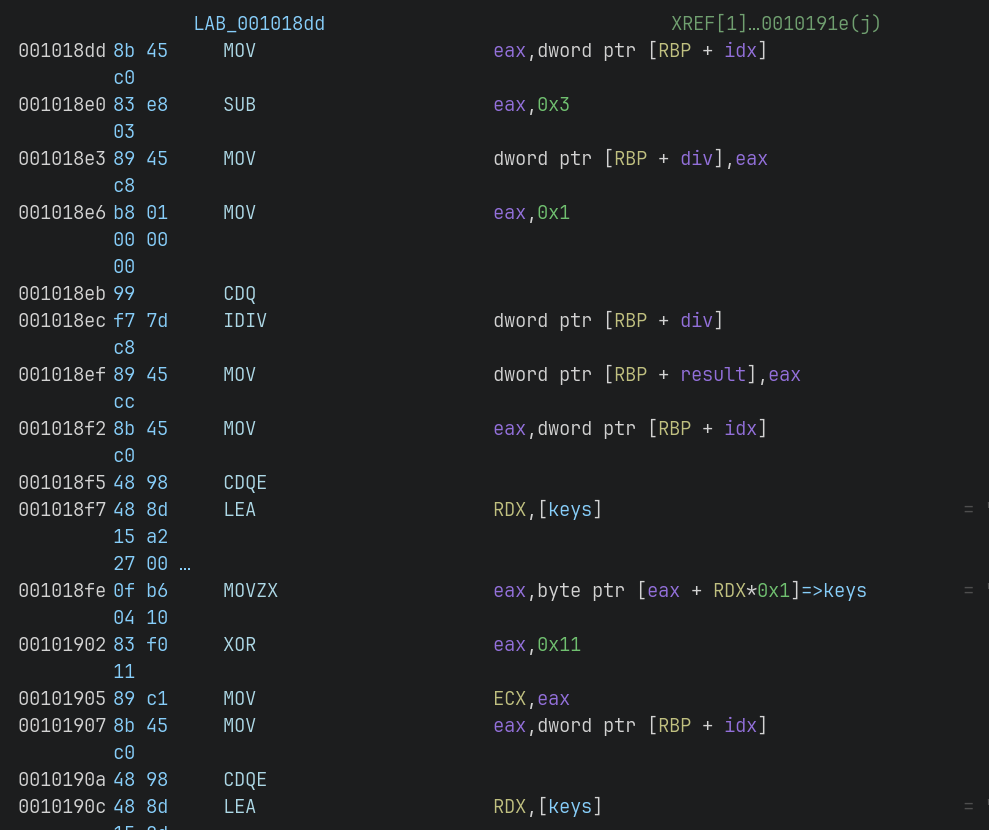
基本思路是四个线程一次执行,那么只要全部反向执行一次就可以解出,从检查函数里找到目标数组,开逆!
直接莽是不行的,比如main函数里还注册了SIGFPE的处理函数,看反编译结果半天没看出哪里会发生除0异常,
最后发现会引发异常的代码没在反编译中出现,它会打断异或处理(即只执行了前3项),
随即进入处理函数,给flag[32] += 1
逆完还是不对,最后在_INIT_1函数里发现作者把"123456"的key字符串替换成了"feifei",这么折腾完,终于拿到flag了
动调终于发现了key有问题
1 | #! python |
ezcpp
cppppppppppppppp
找到main函数中发现有一个对输入的字符串进行处理的函数,拿之后要比对的数据将所有操作全部逆推, 就可以推知flag
1 | // ezcpp.c |
一开始把循环轮次写错了,0x20变成20了,后来发现的时候汗流浃背了(笑)
还有,有个cout就算面向对象了是吧
babyAndroid
jadx一通分析,程序先检查用户,再检查密码,那就逐个击破: 先逆推正确用户,然后解决密码
使用Ghidra FindCrypt发现so里有aes加密,密钥是用户,提取其中的密文,再用正确用户解密, 拿到flag
1 | from Crypto.Cipher import AES |
flag拿到了,但是在app里校验的时候显示密码错误! 你这app写得有问题啊
crypto
midRSA
兔兔梦到自己变成了帕鲁被crumbling抓去打黑工,醒来后连夜偷走了部分flag
padding补在flag后面,并且随后右移了26个字节,意味着先丢失的是padding(大端序表达?), 推测还会有flag剩余,结果一解析...好家伙,padding都没移完
1 | In [2]: long_to_bytes(13292147408567087351580732082961640130543313742210409432471625281702327748963274496942276607) |
非预期,爽!
backpack
crumbling的游戏已经玩到了中期,打算带着帕鲁搬家到新据点,你来帮他研究一下背包管理
由于p是32位的,即4字节的,那么只有4个字节受到影响,前面的字节不受影响,因此可以尝试解析
1 | In [3]: long_to_bytes(871114172567853490297478570113449366988793760172844644007566824913350088148162949968812541218339) |
misc
ek1ng_want_girlfriend
An introducation to Wireshark and also ek1ng.
用Wireshark打开capture.pcapng,发现请求了资源/ek1ng.jpg,跟踪tcp流截取raw数据保存,
然后使用ImHex编辑之,去掉头部的http请求头即可拿到图片

还可以这么找女朋友的吗
ezWord
通过破译图片的水印来解开文档里的秘密吧!
直接使用压缩软件打开word文档,其中的media文件夹中包含了jpg和png两张很相似的图片, 结合提示,推测是盲水印。找到BlindWaterMark项目然后clone下来运行
1 | $ python bwmforpy3.py decode ../downloads/media/100191209_p0.jpg ../downloads/media/image1.png decoded.png |
解码出盲水印:

根据提示将其作为密码提取secret.zip中的secret.txt文件,看到满屏的文本,
推测为电子邮件加密。在spammimic - decode中解密邮件,
得到字符串:籱籰籪籶籮粄簹籴籨粂籸籾籨籼簹籵籿籮籨籪籵簺籨籽籱簼籨籼籮籬类簼籽粆,
解码查看字节:
1 | In [4]: code.encode('utf-8') |
根据utf-8编码规则,三字节一编码,而且flag是hgame开头的,恰好前2个utf-8字符也符合h和g的差值, 那么将所有的字符减去差值就可以找到原始字符串
1 | In [8]: offset = ord(code[0]) - ord('h') |
- 标题: hgame2024 week2 剩余题解
- 作者: RocketDev
- 创建于 : 2024-02-17 21:31:00
- 更新于 : 2024-07-25 12:34:56
- 链接: https://rocketma.dev/2024/02/17/W2_remainder/
- 版权声明: 本文章采用 CC BY-NC-SA 4.0 进行许可。