hgame2024 week1 剩余题解
15 challenges solved
web
ezHTTP
HTTP Protocol Basics
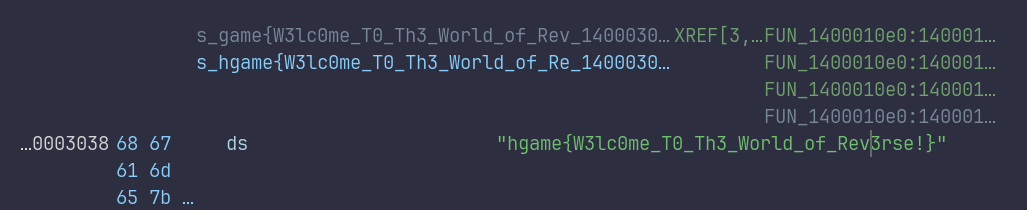
考察http的3种头
然后cyberchef解码高亮的base64文本,找到json标签里的"f14g"字段
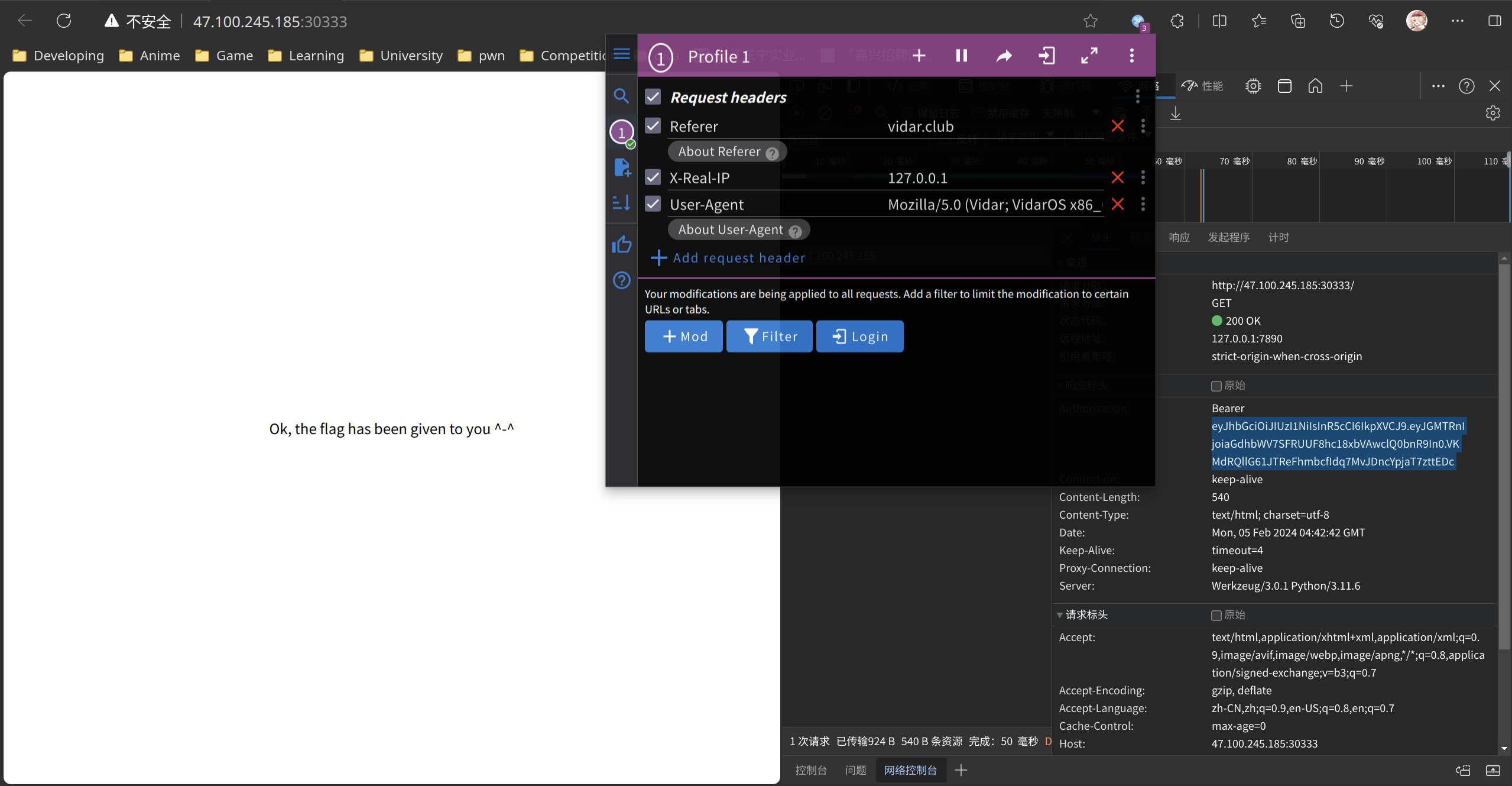
not xff? 所有标准头都试了一遍,不行
结果是X-Real-IP??打pwn打多了导致基础欠缺
Bypass it
This page requires javascript to be enabled : )
在注册的时候发现本来可以注册的,但html里有js阻拦,此时禁用js就可以注册了
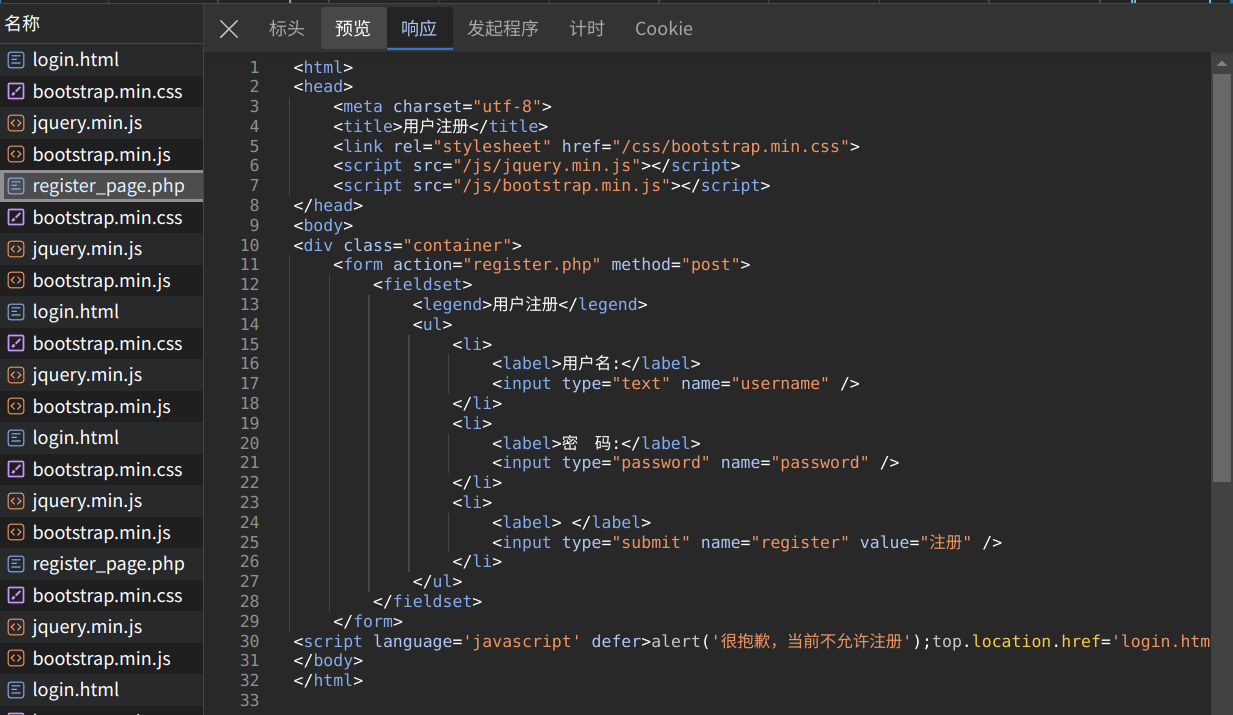
注册完用刚才的账号登录,点击~~click here~~拿到flag
主打的就是一个叛逆
reverse
ezASM
To learn a little ASM
关键代码,看出check中是将[c + esi] ^ 0x22与输入作比较
1 | check_flag: |
取数据c放入ipython中作异或解密为原来的flag
1 | In [18]: d = [74, 69, 67, 79, 71, 89, 99, 113, 111, 125, 107, 81, 125, 107, |
ezPYC
ez python Reverse
先使用pyinstxtractor把exe中的文件提取出来,然后在解密pyc文件得到部分源码
1 | flag = [ 87, 75, 71, 69, 83, 121, 83, 125, 117, 106, 108, 106, 94, 80, 48, 114, |
推测1234是密钥,尝试循环异或解密
1 | In [3]: d = b'' |
ezUPX
UPX is a packer
upx -d ezUPX.exe 拿到压缩前exe,分析main函数
1 | local_38 = ZEXT816(0); |
推测把数据每个异或0x32即可
1 | In [1]: flag = [0x64, 0x7B, 0x76, 0x73, 0x60, 0x49, 0x65, 0x5D, 0x45, 0x13, 0x6B, 0x2, |
ezIDA
Do you know how to use IDA?
逆向即送

没有ida可以用ghidra替代
crypto
ezRSA
一个简单的RSA
根据费马小定理, $p ^ { q - 1 } = 1 (mod\ q)$
所以 $p ^ q = p (mod\ pq)$
题目里给出的leak1和leak2,实际上就是p和q
由p, q, e, c解密rsa
1 | import gmpy2 |
misc
SignIn
换个方式签个到
flag格式:'hgame{[A-Z_]+}'
缩放也可以看到哦
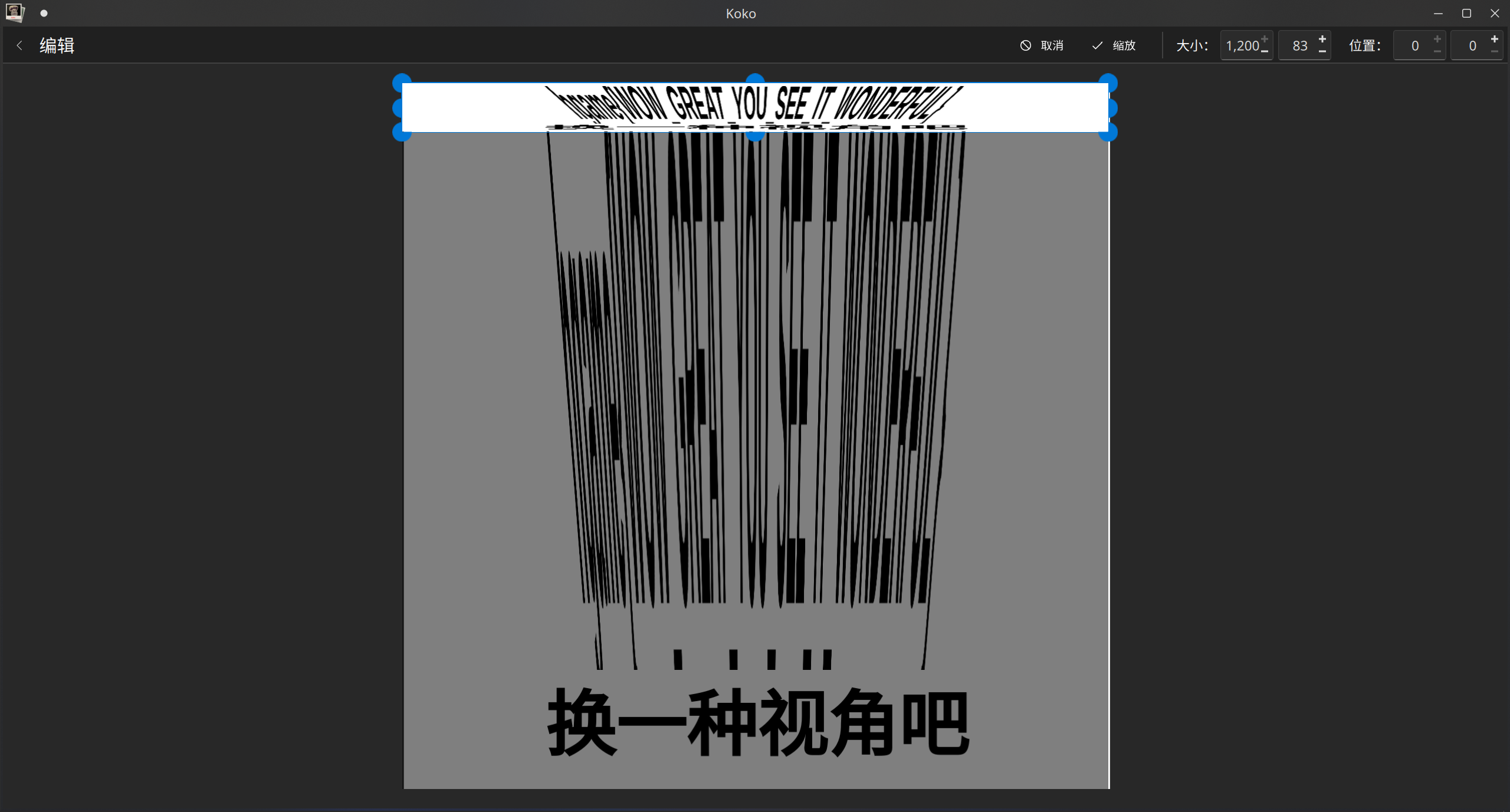
simple_attack
怎么解开这个压缩包呢?
压缩包组成like:
1 | + src.zip |
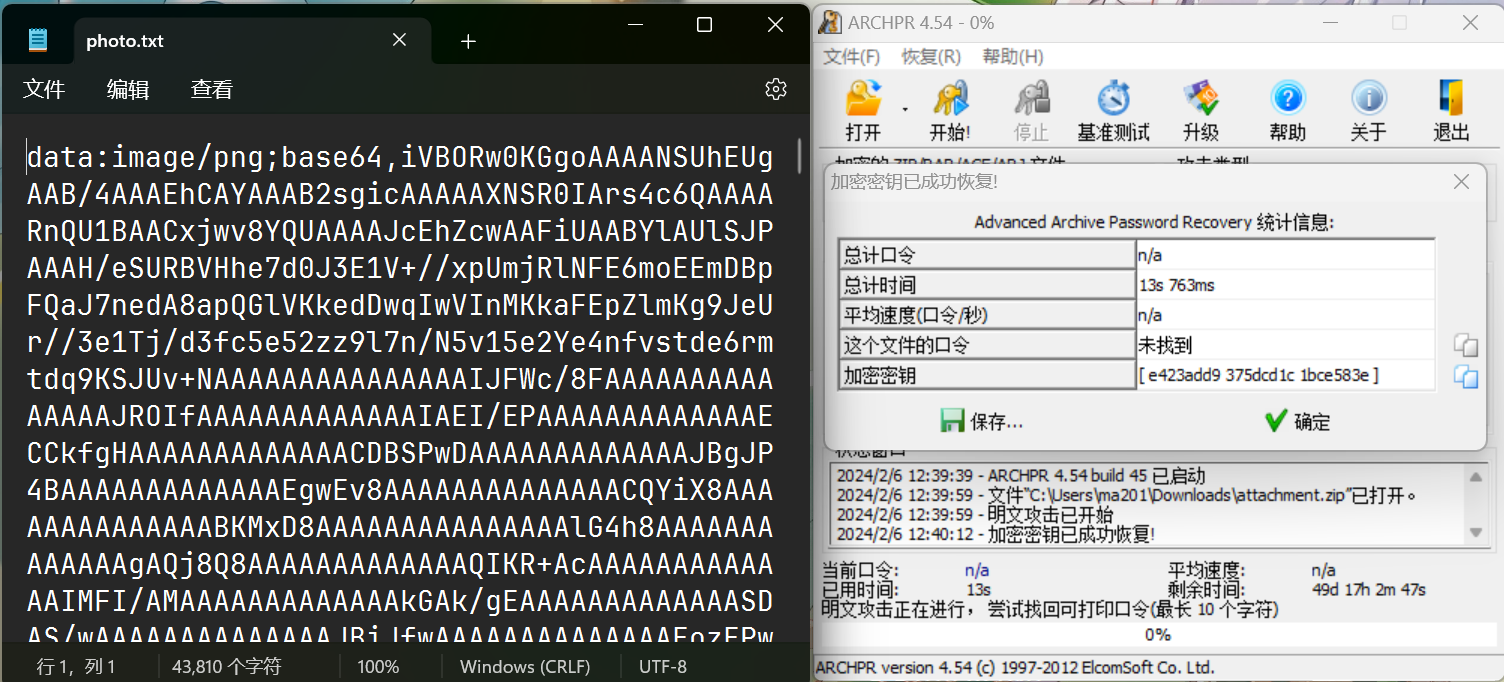
两张图片CRC校验一致,使用azpr明文攻击得到flag
浏览器中打开获得flag

一开始忘了怎么用的,挂了一晚上等它找回密钥, 一停止才想起来早就解密完成了
签到
公众号关注发送消息即得
pwn
EzSignIn
Have fun in pwn games of hgame2024~
nc 连接即得
- 标题: hgame2024 week1 剩余题解
- 作者: RocketDev
- 创建于 : 2024-02-07 19:36:00
- 更新于 : 2024-07-25 12:34:56
- 链接: https://rocketma.dev/2024/02/07/W1_remainder/
- 版权声明: 本文章采用 CC BY-NC-SA 4.0 进行许可。